
How To Tell If Your Computer Is Being Monitored?
How to Tell if Your Computer Is Being Monitored?
Have you ever questioned whether your computer is being monitored? Do you have the impression that anything you installed on your computer is tracking you? There is always the possibility that malicious software installed on your computer will be reported to a hacker.
At some point, we have all had the impression that our computer has violated our privacy. Similar inquisitiveness prompted me to conduct some online study. I've collated my findings as methods for determining whether my computer is being monitored.
If you follow through and discover nothing strange, you can rest assured that you will enjoy a good night's sleep.
How Can An Attacker Gain Access To Your System?
When it comes to monitoring, it is always a computer program that is responsible. Malicious software is constantly being installed on your computer, with or without your agreement. It is unlikely that you will ever need to remove them.
And by then, it may be too late to prevent a breach of your privacy. The most typical way for this software to get onto your machine is via file downloads.
Consider this webpage.
Which button would you click to actually download the file? Yes, I would be perplexed as well if I saw something similar. Frequently, bogus buttons are posted on websites like this. They may not actually download your file for you, but may instead install a program on your PC.
By pushing a button first, you can determine if it is not what you desire. However, are you willing to accept that risk? That is, downloading a file should not be difficult for anyone. Even yet, there are situations when you are unsure whether you obtained the file you sought or ended up with a tracker program on your computer.
If you are not downloading software, the file(s) should NOT be in the exe file type.
How to Tell if Your Computer Is Being Monitored
Here are seven distinct methods for determining whether or not your computer is being monitored.
1. Monitoring processes from Windows Task Manager
1. To start Windows Security, press Ctrl + Alt + Del simultaneously.
2. To launch the Task Manager Window, select Task Manager.
3. If this is the bare-bones view, To access the detailed view, click on More details.
4. Select the Processes tab to get a list of all currently running programs and processes.
Take a thorough examination of your surroundings. This is the most effective method of becoming acquainted with the programs. Ascertain that nothing suspicious is running.
To sort by network activity, click on the Network heading. If you are being watched, the unknown program is almost certain to transfer data across the network.
2. Monitoring Open Ports using netstat
1. From the Start Menu, select Run.
2. Enter the command CMD and press enter to open the command line interface.
3. Type ipconfig to view a list of available network adapters.
4. Make a note of the IPv4 address for each connection profile. There is no need to be concerned about the remaining information. ( Tip : If you're using a virtualization software like VMware or Virtualbox, you'll notice a slew of virtual adapters. This is acceptable.)
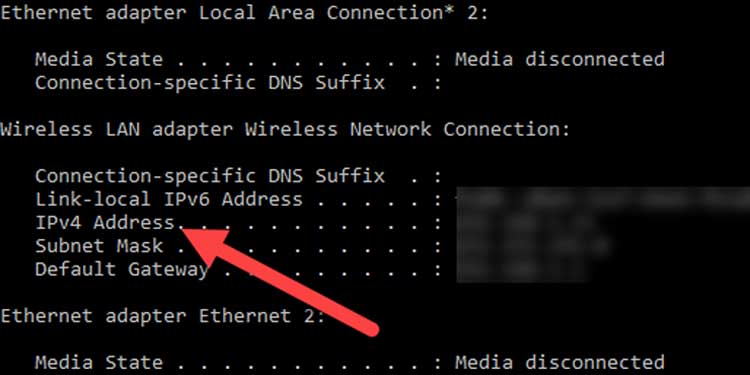
5. Type netstat -an to obtain a list of all open ports and addresses.
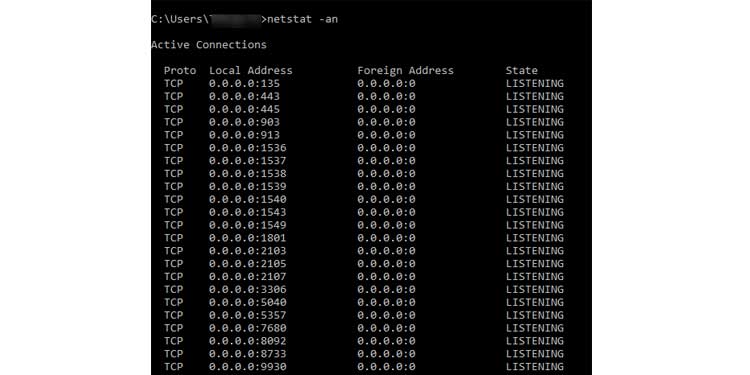
Apart from the IP addresses specified in Step 4, you must ensure that this list contains no new IP addresses. If any are present, it indicates that another computer is connected to yours using Remote Desktop Services. Someone is eavesdropping on your computer.
3. Periodic Antivirus scans
1. Navigate to the Start Menu or use the Search bar.
2. Type 'threat protection' to open the window for Virus & Threat protection.
3. Click on Quick scan to begin scanning your computer for viruses.
4. Alternatively, click on Scan choices. This gives you the option of performing a complete scan or a custom scan.
5. Once it is complete, check your PC for suspicious files or threats.
The built-in virus and threat prevention application does an admirable job at recognizing dangers. Nonetheless, many users opt for stand-alone antivirus software. These tools identify malware and keyloggers, which are used to monitor users.
They are then removed from the system to ensure that the system is always fully protected. Antivirus software is available in both free and premium editions. It is suggested that you get a premium version from a reputable antivirus vendor.
4. Investigating Recent Files
1. From your Desktop or Taskbar, click This PC.
2. On the top left, beneath the navigation bar, click on Quick access to bring up Frequent folders and Recent files.
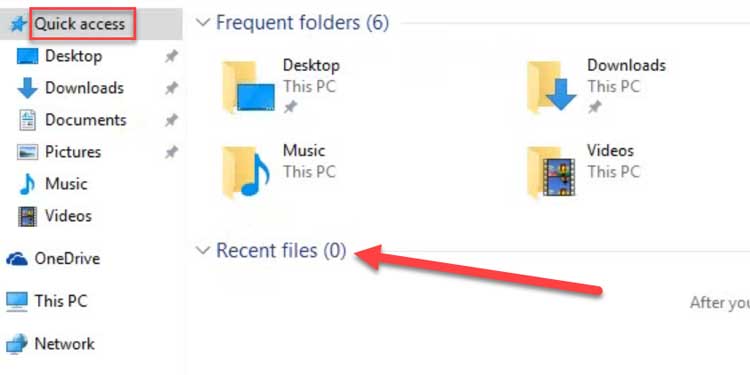
This is the simplest and fastest technique to determine if someone has been monitoring your file system.
The Recently accessed files and folders section displays a list of the most recently accessed files and folders. If you did not open anything in this folder, then it was accessed on your computer by another user.
5. Investigating Browser History
Open your web browser and navigate to the history section (click Ctrl + H or Ctrl + Shift + H).
This is another fast approach to determine whether someone has used your computer maliciously. For an extended period of time, the browser keeps track of all websites visited on your computer. Again, if you notice anything odd, it's likely that someone else has accessed your computer.
However, if the perpetrator uses Incognito mode, this strategy is useless. Bear in mind that Incognito mode clears the browser's history. In any case, repeat this procedure for all browsers installed on your computer, not just the ones you use.
6. Auditing Login Event Viewer
Additionally, you may view login events to determine whether someone remotely logs in and out of your computer. To accomplish this, perform the following:
1. From the Start Menu, type 'Windows Administrative Tools' to open a new window.
2. Double-click on Event viewer to activate the application.
3. Select Windows Logs from the left navigation pane. After that, double-click Security to bring up all Security events.
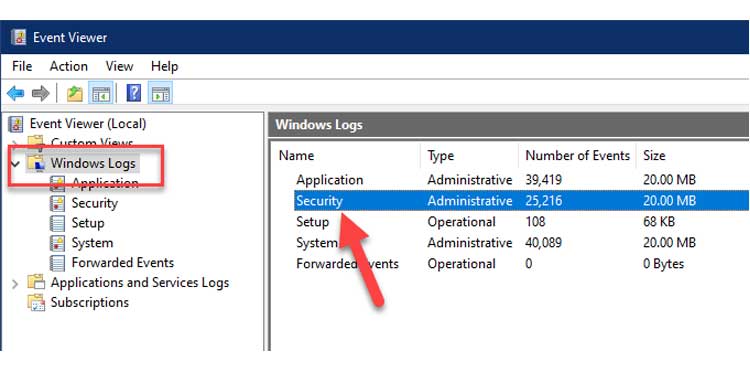
4. Perform a search for any event(s) containing the Task Category Logon/Logoff. You can narrow the search to a certain date and time range to aid in the process.
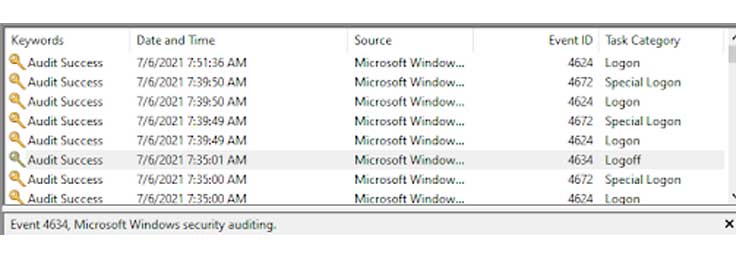
You must look for a login for the Administrator group. However, a trail of SYSTEM and BACKUP logins is common. If you discover anything unusual in the logs, you're in big danger. Someone is continuously logging in and out of your system and watching your activity.
7. Identifying Corporate Monitoring
This is the most 'legally permissible' form of surveillance. If you do not own the computer on which you are now working, you are technically using someone person's computer. This someone may be the corporation for which you work.
Businesses employ a variety of strategies to safeguard their trade secrets and other valuable assets. As a result, it's only logical for them to install monitoring software on the machines they own. The IT team is legally authorized to install programs on the company's personal computer.
It's understandable that they're doing this to safeguard the business and its data. They may install a variety of applications. Certain applications may solely report on system resource utilization. Others can record keystrokes and application activity. Some companies even go so far as to provide remote access to the IT department.
This does not necessarily imply that they will be careless with your personal information. A good organization will constantly adhere to privacy issues and requirements.
Generally, installed apps run in the forefront. Unlike viruses, they also make no attempt at concealment. These programs are likely to be running in the taskbar or task manager. However, this can vary depending on the type of program.

