What is a Penetration Testing and Why Do I Need it
What is Penetration Testing and Why Do I Need It? The shocking reality is that security breaches have increased by approximately 67 percent in the last five years, and the likelihood of additional companies being hacked is high. By the end of 2021, the global cost of cybercrime is expected to reach $6 trillion. The good news is that penetration testing can serve as a first line of defense against cyber-attacks. However, what is penetration testing and why is it necessary? This post will define.
The Top Four Reasons for Database Data Loss and what to do about it
The Top Four Reasons for Database Data Loss (and what to do about it) IT security practitioners are well aware of the importance of data loss prevention (DLP). These risks do not go away as organizations adopt cloud-based managed database services such as Amazon RDS and Amazon Redshift; in fact, they become more serious in many ways. While AWS takes security of their infrastructure extremely seriously, individual customers are responsible for securing their own data and access to it. Typically.
Is It Time to Consider Replacing Your CDN?
Is It Time to Consider Replacing Your CDN? Content Delivery Networks (CDNs) serve as the Internet's pipelines. They are reshaping how information is consumed online behind the scenes, accelerating web traffic, enhancing user experience, and enabling every website to truly go global. As you might imagine, any technology capable of causing such seismic shifts in the way people conduct business is bound to encounter obstacles. Many industries are currently engaged in an internal debate about futu.
Instructions on how to build a security-first culture with remote teams
Instructions on how to build a security-first culture with remote teams The increased number of remote workers in your organization as a result of recent world events means that already overburdened security teams and overworked IT departments will be faced with even more challenges in terms of security. Sixty-one percent of CISOs are more concerned about security risks aimed at employees than they were prior to COVID [IDG], with a significant portion of this concern stemming from employees wor.
What is Management Information System (MIS)?
What is Management Information System (MIS)? MIS is the Study of People, Technology and Organizations. If you enjoy technology like iPhones, Amazon Echo and Instagram, you have what it takes to study information systems. All that is required is an interest in technology and a desire to use it to better people's lives. Many people believe that MIS is entirely about programming. However, programming is only a small part of our curriculum, and there are numerous jobs in information systems that d.
4 features your data-centric security strategy must provide
4 features your data-centric security strategy must provide Following the advent of the big data movement at the turn of the twenty-first century, technological advancements enabled businesses to manage, store, and process unprecedented volumes of data. Almost all organizations face significant security risks as a result of the exponential growth of data generated and stored. Businesses must develop a data-centric security strategy to equip security teams and other stakeholders with the tools n.
5 Ways to Make an Impression During Your CISO Job Interview
5 Ways to Make an Impression During Your CISO Job Interview What does a global CISO role entail? Although technology skills, competence, and awareness are clearly important, here are five other areas where you can stand out during the hiring process. 1. You’ve made it to the top – but can you take it to the board? Tech-savvy board members are rare. A successful CISO knows how to present cybersecurity threats, risks, and mitigation in a business-focused manner. To impress .
5 reasons why depending on your ISP for DDoS protection is a bad idea
5 reasons why depending on your ISP for DDoS protection is a bad idea A distributed denial of service (DDoS) attack is a malicious attempt to disable an online service for users, typically by temporarily interrupting or suspending the hosting server's services. Once considered a prank, DDoS attacks are now frequently used by cybercriminals to earn money. They are regarded as one of the most powerful weapons on the internet due to their ability to be launched at will, impact any aspect of a webs.
Things to note about DevSecOps
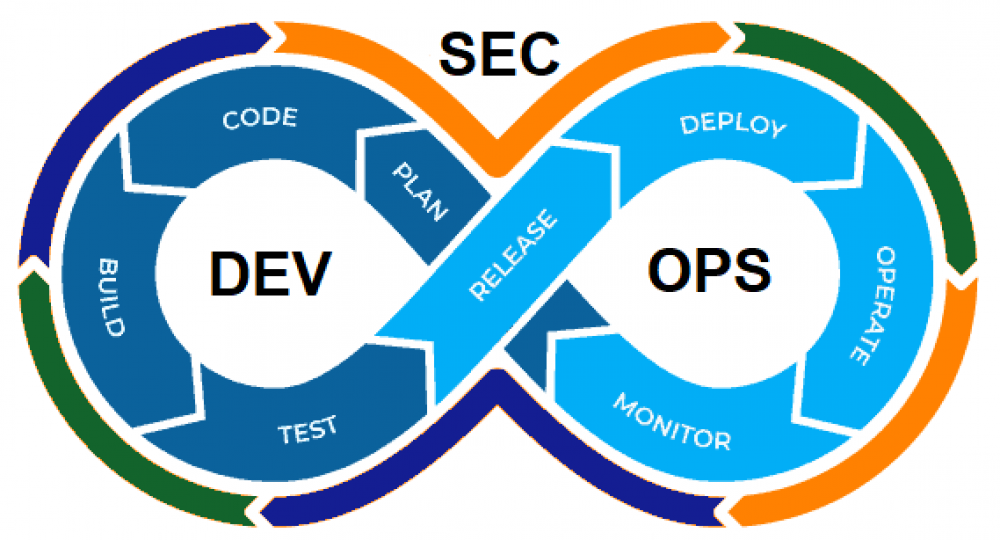
Things to Note About DevSecOps The majority of those in the IT and software industries are familiar with DevOps and its framework for integrating development and operations. DevOps has evolved into a standard for ensuring continuous software deployment in response to customer needs. However, the process is not limited to development and operations. Security must be considered as well. As a result, when it is combined with the other two, we now have DevSecOps. What Is DevSecOps? To sum.
Why it is possible that you will notice subtle changes to the design of your smartphone
Why it's possible that you'll notice subtle changes to the design of your smartphone The smartphone season has begun, and the headlines will almost certainly be the same as they have been in the past: thinner, sleeker, and faster models are on their way to consumers' hands. However, if a new push from the United States government is successful, future smartphones may be required to include an additional feature: the ability to be repaired in whatever manner the device owner chooses. It could a.