My Mobile Take Photos by Itself and How to Avoid It
My Mobile Take Photos by Itself and How to Avoid It? Although it may appear to be something out of science fiction, some users have discovered that their mobile phone takes photos even when they are not physically present. This is easily discovered by accessing the smartphone's gallery and observing how photos that we did not take appear in our gallery with the date and time they were taken while we were not even using the phone. This can be frightening, but it is not always the case, and on o.
Moto E-Series Smartphone
Moto E-Series Smartphone Renders of an unnamed Motorola smartphone have allegedly surfaced on the internet, showing dual rear cameras and a waterdrop-style notch. Renders of an unnamed Motorola smartphone have allegedly surfaced on the internet. These renders were shared by a tipster via a tweet, but there is no mention of the smartphone's name in the tweet. Based on the design of the Motorola smartphone, it is possible that it is a member of the Moto E series of smartphones. Motorola is report.
Java vs JavaScript: Differences Between Programming Languages
Java vs JavaScript: Differences Between Programming Languages When completing a project, we have a large number of programming languages from which to choose. However, not all of them will be beneficial to us, depending on the project's objectives. There are programming languages that are optimized for web development, others that are optimized for game development, and still others that are optimized for designing programs for the PC or mobile phone. While it is frequently straightforward to d.
They Can Steal Your Passwords and Breach the Bank in a Moment
They Can Steal Your Passwords and Breach the Bank in a Moment We can say that while password theft is common on the Internet, it has become more difficult for cybercriminals over time. The two-step authentication methods are critical. Essentially, that second code that you must enter. As a result, even if they have the access code, they will be unable to enter without performing the second step. Now, in this article, we're going to discuss Robocalls and how they can quickly steal our credential.
How to Prevent Unauthorized Installation of Apps
How to Prevent Unauthorized Installation of Apps Malware, viruses, and other malicious programs are a daily occurrence that affect hundreds of mobile devices and cause significant inconvenience to their users. And, while Google's operating system is more secure against these threats, the reality is that it is not impenetrable and may contain some vulnerabilities that cybercriminals or hackers can exploit. One of the most common entry points for this type of malicious user is through the instal.
How to Avoid Google Drive File Sharing Spam
How to Avoid Google Drive File Sharing Spam Spam is one of the issues that we encounter when we surf the Internet. The norm is that it reaches us via email, which includes all the junk e-mails we receive on a daily basis, but also via other channels such as SMS, social media, and so on. Among them is Google Drive, the cloud-based storage platform. We'll explain what this issue is and how to avoid Spam in Drive. Why Is Spam an Issue in Drive? Spam is a general term that refers to all s.
Fast charging support for the Google Pixel 6 and Pixel 6 Pro is expected to be 33W
Fast charging support for the Google Pixel 6 and Pixel 6 Pro is expected to be 33W According to a new report, the Google Pixel 6 and Pixel 6 Pro may be equipped with fast charging capabilities of up to 33W. A few details about the two phones were revealed earlier this month by Google, which also shared some of the phones' specifications. Now, some information about their charging capabilities has surfaced, following reports that the Pixel 6 series will ship without a charging brick in the box w.
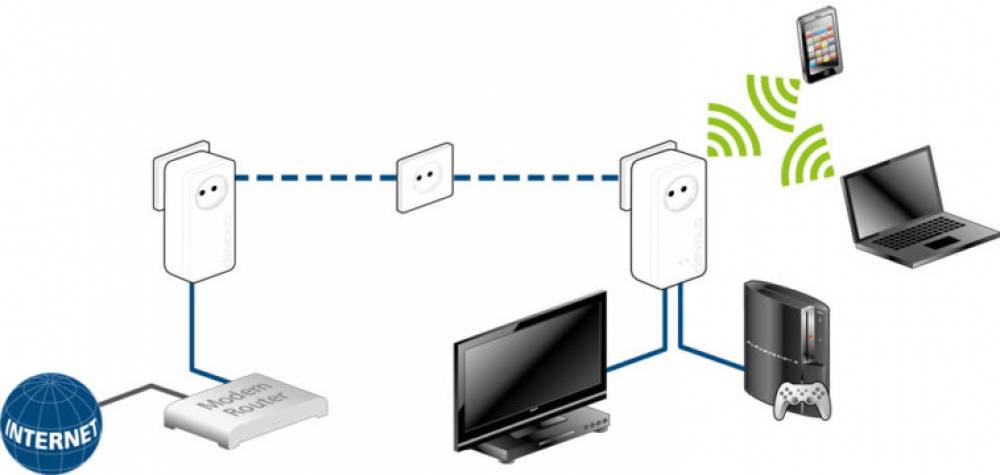
Everything You Must Avoid When Using PLC Devices to Boost Wi-Fi
Everything You Must Avoid When Using PLC Devices to Boost Wi-Fi We can use a variety of devices to improve Wi-Fi connections. Typically, a repeater or amplifier is used, but we can also use mesh systems or PLC devices. This article discusses the latter. We're going to outline the most common errors that should be avoided in order to ensure that they operate as efficiently as possible. Thus, the wireless network will maintain its speed and stability. Frequently occurring failures when using PLC.
Is it possible to achieve the same speed using Wi-Fi and a repeater
Is it possible to achieve the same speed using Wi-Fi and a repeater Today's Wi-Fi devices enable us to move more freely within our homes. The issue is that not all locations have strong Wi-Fi reception. This can make using the Wi-Fi equipment in those rooms or rooms a real ordeal. Typically, the issue is caused by a router that is incapable of providing all of the coverage we require. In these cases, the simplest solution is to install a Wi-Fi repeater that amplifies the signal so that we can c.
Apple has been asked by policy groups to abandon plans to inspect iMessages and scan for abused images
Apple has been asked by policy groups to abandon plans to inspect iMessages and scan for abused images In an open letter published on Thursday, more than 90 policy and human rights organizations from around the world urged Apple to abandon plans to scan children's messages for nudity and adult phones for images of child sex abuse and instead focus on other important issues. According to the letter, which was first reported by Reuters, "Though these capabilities are intended to protect children.