
How To Protect Your Privacy On Android Phones
How to protect your privacy on Android Phones
Nowadays, we store a great deal of personal information on our mobile devices, and as a result, these devices know a great deal about us. We happily exchange some of this information, from our location and contacts to our favorite hangout spots and hobbies, for “free” services from companies like Google and others, but there are plenty of less scrupulous individuals and businesses out there who would also like to get their hands on this valuable asset.
Nowadays, it makes sense to safeguard the data stored on your smartphone, and fortunately, the Android ecosystem includes a plethora of useful tools for doing so.
Make use of the lockscreen

Using a simple PIN, password, or swipe gesture is truly the bare minimum level of security that every smartphone user should implement. As shocking as it may sound, data from a reputable survey conducted in early 2016 indicated that 34% of all Android users do not even use the built-in lockscreen feature on their smartphones. While this figure has likely increased since then, it demonstrates an important point: not everyone takes security as seriously as they should.
While malicious software, bugs, and backdoors frequently make tech headlines, physical phone theft continues to be a problem. If a criminal lacks the decency to steal your phone, they are unlikely to have any reservations about sifting through your contacts, photos, and emails in an attempt to obtain personal data for further exploitation. There's a good chance you're also using a banking app on your phone, and you'd really hate for someone to gain access to those types of vital and personal apps.
To enable a lockscreen PIN, navigate to Settings -> Security -> Screen Lock. Choose your preferred password lock type here, which you will then be required to enter each time you attempt to access your phone. Other manufacturers may relocate this menu to the general settings section if they offer an alternative to lockscreen protection, such as LG's knock code. And, of course, many phones now allow you to log in using alternative methods such as your fingerprint, if passwords aren't your thing.
Device Encryption

Applying a password to your phone's lockscreen is a start, but particularly nefarious and skilled criminals may still be able to access your files if they have enough time and access to a stolen smartphone, for example. Device encryption can be used to encrypt all of your files in a way that they cannot be read without first being decrypted using the appropriate key or a password that only you know.
Encryption is an extremely difficult form of security, which is why the FBI is battling Silicon Valley firms in an attempt to circumvent it. However, it comes at a performance cost on some older smartphones, though users of newer devices should notice no difference.
As with the lockscreen, encryption options are found in the Settings -> Security menu, where you can protect both your smartphone's internal storage and a microSD card, if your device has one. Encryption can take some time, so it's best to begin with a fully charged battery and plenty of time to spare.
Find my device
While we're on the subject of preventing stolen smartphones, all Android users should take a moment to familiarize themselves with Google's Find My Phone feature. Previously known as Android Device Manager, this service is integrated with your Google account and allows you to remotely manage all of your Android devices, as long as they are connected to the internet.
Find My Device can be accessed via this link from any web browser. From here, you'll see a list of your devices, along with options to track their location, make them ring in case your phone becomes lodged in your couch, or "enable lock and erase." By enabling this final feature, you'll be able to remotely lock and wipe your smartphone or tablet's memory if it's stolen.
These same settings are also available directly on your device. Navigate to "Google Settings" and select "Security." You can review and edit remote locking and erasing options under Find My Device.
Picking tougher passwords
Along with not using a lockscreen, using weak or frequently used passwords is a big no-no if you want to keep your data secure on device and online. Lists of the most frequently used passwords are published on a fairly regular basis, and if your preferred password appears on one of these lists, you should definitely change it.
As a general rule, a password that contains a mix of upper and lower case letters, numbers, and special characters (where permitted) is the most secure, and the longer the better. While eight characters is the bare minimum recommended, increasing them to twelve or sixteen makes them significantly more difficult to guess.
While a strong password is recommended, using multiple passwords is even better. You've almost certainly heard about websites being hacked and passwords being exposed, so it's risky to rely on the same code for all of your accounts, apps, and websites these days. Naturally, keeping track of all these different passwords can be a nightmare, but there are a number of apps available that can assist in managing them and even generate extremely strong random passwords.
Android applications such as LastPass, mSecure, oneSafe, and Keepass2Android each offer their own set of unique security features. Among them are secure password storage, two-factor authentication, and multi-device support.
VPN (Virtual Private Networks)

Thus far, we've focused primarily on offline security and preventing thieves from accessing your private files. However, it is possible for the bad guys to monitor what you are viewing and downloading online.
Utilizing a Virtual Private Network is one way around this (VPN). Rather than communicating directly with each website, a VPN service routes your traffic through a different server or group of servers first. This prevents your IP address and device from being immediately associated with an end service, though it does not preclude someone from following the chain further back if they are truly interested in what you were doing. Certain VPNs will also log your activity, so it's always a good idea to read the terms and conditions before using any service.
VPNs provide an additional layer of privacy, but they do not completely conceal your identity. Additionally, they are frequently used to access websites that are region-locked, such as on-demand video streaming services. However, you will frequently notice that your internet speeds slow significantly as a result of the diverted traffic.
Understanding App Permissions
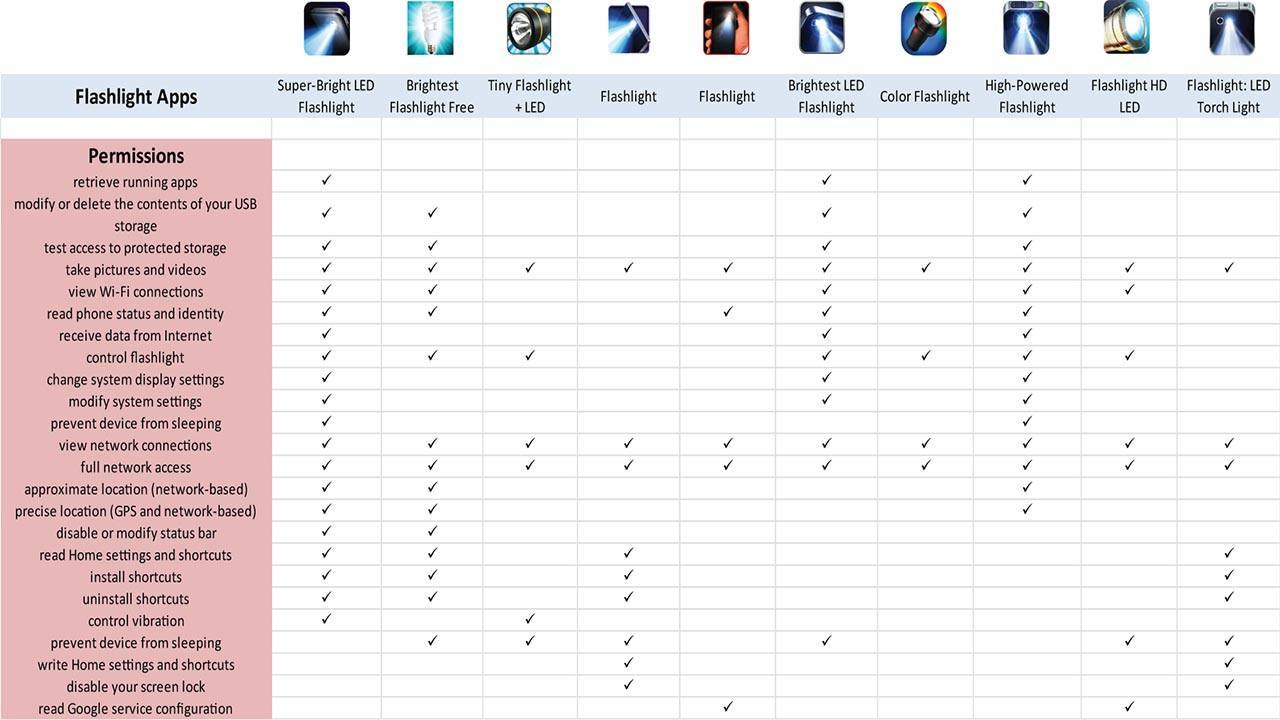
After discussing data privacy in general, the other major snoopers in the mobile space are the apps that we all download. Of course, you should always install software from reputable sources such as the Play Store, but even then, some apps, particularly those that are free, exist to profit from your data. Ad-supported applications are one thing; rooting around in your files is quite another.
One major indicator that an app is up to something fishy is to examine the permissions that the app requires upon installation and consider what makes sense for the features offered by the app. A classic example is the abundance of popular flash-light apps, many of which require access to USB storage, WiFi networks, data, and Google services that have nothing to do with turning on or off a flash-light.
Unfortunately, this is a somewhat gray area, with some permissions required to perform tasks that may not appear to be critical to the app's primary purpose. Although top-tier app developers should explain why specific permissions are required in the app's description, this is not as common as it should be.
With the introduction of Android Marshmallow, users can now actively manage the permissions granted to apps. Simply navigate to Settings -> Apps -> click the gear icon -> App Permissions to accomplish this. However, not all apps have been updated to use the latest Marshmallow API, and thus disabling some permissions may cause older apps to fail to function properly. Expect to spend some time here experimenting.
Anti-virus apps
While the Play Store does an excellent job of filtering out malicious applications, additional security can be obtained through the store's selection of anti-virus applications. This is not strictly necessary for the majority of users, but if you frequently download apps from other developer websites, anti-virus software is certainly worth investigating.
Of course, the free versions are likely to collect data for the purpose of selling it for advertising purposes, defeating the purpose of our article. However, there are several reasonably priced options that include some additional features.
Numerous anti-virus apps now include anti-theft features, such as remote phone locking and wiping, similar to the Find My Phone feature. Additionally, some of these apps can monitor for broader Android security vulnerability exploits, such as Stragefright, and provide protection against malicious emails and malicious websites, which are not easily covered without an anti-virus app.
In Conclusion
That is a lengthy list, but there are numerous small things you can do to protect your privacy and help keep your Android devices more secure. Along with the apps and settings mentioned previously, perhaps the most effective change you can make is to adjust your phone habits. Keep location usage to a minimum, disable or uninstall unused apps, keep an eye on app permissions during updates, and regularly change your passwords, and you should be safe.
Courses and Certification
Android Programming Course and Certificate
Mobile Computing Course and Certificate
Mobile Development Course and Certificate
Mobile Marketing Course and Certificate
Mobile Security Course and Certificate
Mobile Testing Course and Certificate
Information Security and Cyber Law Course and Certificate

